Think your data is safe? Think again.
Cyberattacks are becoming more and more sophisticated, and organizations are falling behind when it comes to defense. In fact, according to recent data from Symantec, around half a billion personal records were stolen or lost through company data breaches in 2015.
Hackers are becoming astonishingly clever, and can now get data even from air-gapped computers—those which are not even connected to the internet or to each other.
For example, researchers at Ben-Gurion University have discovered that it is possible to extract data from computers using the sounds of their cooling fans!
To do this, a computer must first be infected by malware. The malware can adjust the speed of the computer’s cooling fan by around 100 Hz. The fluctuations in the speed would be undetectable to anyone using the computer, but a hacker listening in with a receiver can use those fluctuations to read 1s and 0s, and all of your confidential data.
While the technology used to accomplish a feat like this is quite astonishing, it is also pretty frightening realizing that hackers are actually using techniques like this to steal data in the real world.
What can you do about it? Here are some tips for boosting data security at your organization!
1. Keep Your Anti-Virus Software Up-To-Date And Running
First things first—any computer which is ever connected to the internet can theoretically be infected by malware or viruses. Symantec reports that three-fourths of all websites have vulnerabilities which hackers can exploit. Even if you cut the cord, you could still have viruses on your computer.
For that reason, it is essential to run up-to-date antivirus software routinely on all of your computers, even if they are currently air-gapped. This can protect you from even the most unusual and sophisticated attacks, like the fan method the Ben-Gurion University researchers came up with.
Pro Tip: Check out the latest endpoint security programs. They're the latest evolution in a line of programs like anti-virus, anti-malware and anti-spyware.
2. Use Cable Management Access Flooring To Keep Your Networks Separate

Another smart practice is to install cable management access flooring to maintain different levels of security. For example, if you are in the military or government sectors, you probably have a secure and non-secure network, maybe even in the same building. To keep them completely separate from each other, you can use Cat5e cables and separate routers, and place them in isolated cable raceways.
Some administrators shy away from the idea of wired networks, but they are a lot less vulnerable. And nearly every Enterprise-grade network is wired.
With cable access flooring, they are neither an eyesore nor a tripping hazard, since the wires run underneath your floor!
3. Have Policies In Place For Data Backups And Restoration
What if the worst should come to pass and you lose all of your data? All hardware fails eventually, so this is an eventuality you should be prepared for. Most companies make regular backups to a remote server (do this daily if you can). But where many go wrong is data retrieval. They don’t have a plan in place for quickly re-uploading all their data and incorporating it back into their database systems.
Any delay in that process of data retrieval can lead to a lot of lost time and money. So make sure you have a plan in place to get things back up and running as quickly as possible.
Pro Tip: If you don't have a way to restore your data, your backups are useless.
4. Set Up Access Control At Your Facilities

When you think about protecting your data, you may spend a lot of time thinking about the “soft” layers of security. But the physical measures you take are just as important. We already talked about how cable access flooring can help you to protect your secure networks—now let’s talk about who you let into your buildings.
Security for your data physically starts at the gate to your facility. Going back to the example of the fan attack, there are at least two security breaches which make such an attack possible. The first is malware; the second is poor access control. For the fan method to work, a hacker needs to be listening to the physical sound of the fan with a receiver. That means that he somehow needs to gain entry to the server room.
So make sure that you have the right technology in place to prevent such an incursion. The only people allowed into the physical room with your computers should be those who have the clearance level to be there.
Pro Tip: Physical security isn't much good if you don't test it. Like fire drills and emergency drills, routinely testing your security systems is vital.
5. Train (And Test!) Your Staff
Finally, along with the soft and physical layers of security, we cannot forget the human factor. Even the best security plan in the world will fail if the personnel in charge of implementing it are not on the same page. These are the people you rely on to enforce access control and anti-virus updates.
They are in charge of setting up and maintaining your cable access floors and data backup and retrieval plans. So hold regular staff meetings to ensure that everyone in charge of security is technology-literate and knows the right protocols!
Maintaining airtight security in an era of sophisticated cyber-attacks is a challenge, but it is possible to thwart even the savviest hackers. Review your protocols, ramp up your physical security, and make sure you trust the right people with the job!
Pro Tip: The government and military routinely train and test their personnel on cybersecurity. You should too. An easy way to start is by sending a fake phishing attempt using Duo Insight. It's Free.
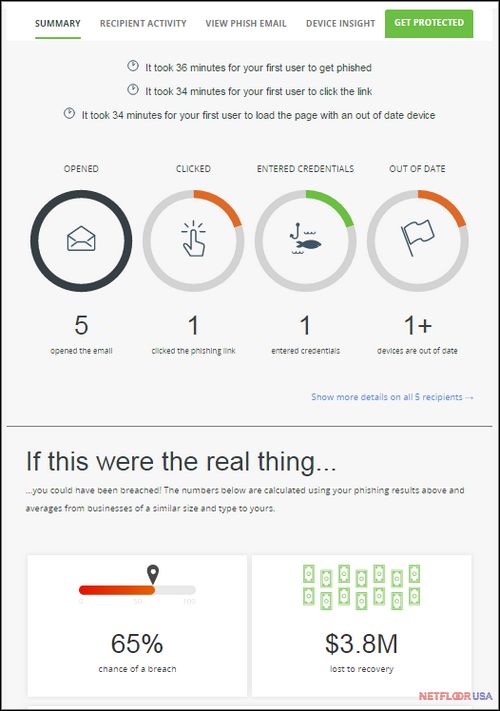
There you have it: 5 steps you should take (all the time) to boost the hard and soft layers of security in your network. For more tips, check out our blog, or read some in-depth articles about networking, IT, access floors and integrated power & data systems.





 Facebook
Facebook Twitter
Twitter Google+
Google+ LinkedIn
LinkedIn